Our Frameworks
Select any framework below to find out more.
ACSC is a small framework on 23 controls designed to provide strategic guidance on how organisations can protect their systems and information from cyber threats.
Applicability Australia.
The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations mitigate cyber security incidents caused by various cyber threats. The most effective of these mitigation strategies are known as the Essential Eight
It has been created on the basis that to achieve full compliance to level 2, you complete level 1 and 2, and to complete compliance to level 3, you must also complete levels 1 and 2.
ACSC ESSENTIAL EIGHT (Aus)
The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) has developed prioritised mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations mitigate cyber security incidents caused by various cyber threats. The most effective of these mitigation strategies are known as the Essential Eight.
The Essential Eight framework within SAM for Compliance has three function levels, 8 categories representing the Essential Eight maturity areas and 8 workplans containing 47 controls. Each control has been assigned a level in accordance with the maturity model. All three levels must be fully achieved to attain full compliance.
More Information Request a demo
The Australian Energy Sector Cyber Security Framework (AESCSF) has primarily been established to develop a tailored cyber security framework, and supporting tools to set the foundation for the future of energy cyber security in Australia.
The framework implementation within SAM for Compliance has 11 Categories, 37 Work Plans and 282 controls. It includes all three maturity levels.
More Information Request a demo
The purpose of the Australian Government Information Security Manual (ISM) is to outline a cyber security framework that organisations can apply, using their risk management framework, to protect their information and systems from cyber threats.
This standard is applicable to Government Departments, their suppliers and service providers.
AUSTRALIAN GOVERNMENT CYBERSECURITY
MANAGE, TRACK AND REPORT IN REAL TIME, AND DEMONSTRATE COMPLIANCE WITH AGISM USING SAM for COMPLIANCE
The purpose of the Australian Government Information Security Manual (ISM) is to outline a cyber security framework that organisations can apply, using their risk management framework, to protect their information and systems from cyber threats.
The ISM is intended for Chief Information Security Officers (CISOs), Chief Information Officers, cyber security professionals and information technology managers.
The ISM represents the considered advice of the Australian Cyber Security Centre (ACSC) within the Australian Signals Directorate (ASD). This advice is provided in accordance with ASD’s designated functions under paragraph (1)(ca) of section 7 of the Intelligence Services Act 2001. The ISM contains various cyber security guidelines. These guidelines cover governance, physical security, personnel security, and information and communications technology security as they relate to the protection of information and systems.
SAM-AGISM has been designed to represent the sections and sub-sections within the ISM and consists of 6 function areas, 22 categories, 380 workplans and 843 controls.
More Information Request a demo
The CERT Top 10 are CERT NZ’s critical controls designed to help organisations decide where best to spend time and money. They have been developed based on data and insights received by CERT NZ from reports and international threat feeds.
72 controls. Applicability New Zealand.
Frameworks for Controls version 7.1 and version 8 are available within the SAM for Compliance system.
CIS (Pure) only contains the CIS controls as defined by the Centre for Internet Security. It does not integrate the guidance and allows an organisation to define their own criteria in order to assess conformance to the CIS Controls.
The controls within our CIS Controls version 8 system are derived from the CIS Controls 8 Safeguards as well as the recommendations contained within the Safeguard descriptions. These form a comprehensive guidance set for the establishment of CIS Controls v8.
MANAGE, TRACK AND REPORT IN REAL TIME, INFORMATION ASSET RISK AND DEMONSTRATE COMPLIANCE USING SAM for COMPLIANCE
COMPLIANCE WITH CIS CONTROLS
The Center for Internet Security (CIS) is a not-for-profit organization dedicated to enhancing the cyber security readiness and response among public and private sector entities. Utilising its strong industry and government partnerships, CIS combats evolving cyber security challenges on a global scale and helps organizations adopt key best practices to achieve immediate and effective defenses against cyber attacks. CIS is home to the Multi-State Information Sharing and Analysis Center (MS-ISAC), CIS Security Benchmarks, and CIS Critical Security Controls. CIS, in association with the City of London Police and the Office of the New York County District Attorney, is a founding partner in the Global Cyber Alliance, an international cross-sector effort designed to confront, address, and prevent malicious cyber activity.
The CIS Controls are:
- Clearly defined and practical controls
- Technically focused to deliver measurable improvement;
- Designed with input from cybersecurity practitioners around the world, and
- Categorised into Implementation Groups suitable for any sized organisation.
CIS Controls is a recognised, best practice Standard which is reviewed and updated regularly, and has global support from cybersecurity professionals. The SAM-CIS Controls frameworks allows you to assess, manage, track and report on your compliance against the CIS controls. SAM for Compliance has CIS Controls v7.1 and CIS Controls v8 available under separate subscriptions.
If you would like to know more about how CIS Controls can help you organisation improve cybersecurity click on the buttons below to request further information or book a demonstration.
More Information Request a demo
CMMC is a standard derived from NIST SP 800-171 to protect Controlled Unclassified Information. It focuses on the CMMC model which measures cybersecurity maturity with five levels and aligns a set of processes and practices with the type and sensitivity of information to be protected and the associated range of threats.
The framework consists of 999 controls derived predominantly from NIST SP 800-53. CMMC Guidance and CIS Controls are also used.
More Information Request a demo
The Government Chief Privacy Officer has issued core expectations of government agencies that represent good practice for privacy management and governance. The framework comprises of 420 requirements and is based on a 5 tier maturity model.
Agencies are expected to implement the good practice outlined in the expectations in a way that reflects their information holdings and systems.
More Information Request a demo
The HISO 10029:2015 is a health and disability sector-wide Health Information Security Framework that advises how health information is created, displayed, processed, transported, has persistence and is disposed of in a way that maintains the information’s confidentiality, integrity and availability.
It is concerned with the security of health information wherever it may exist and is a large framework with 681 controls applicable to the NZ health sector.
More Information Request a demo
The primary purpose of this Information Management Maturity Assessment (IM Maturity Assessment) is to help public offices and local authorities to assess the strengths and weaknesses of their information management (IM) programmes to determine where improvements are most needed.
This is a pragmatic, small framework comprised of 70 requirements contained within 22 categories.
More Information Request a demo
ISO 22313 : 2012 is the International Standard for business continuity management systems and provides guidance based on good international practice for planning, establishing, implementing, operating, monitoring, reviewing, maintaining and continually improving a documented management system that allows organizations to prepare for, respond to and recover from disruptive incidents when they arise.
This Standard is reproduced under licence with permission from Standards New Zealand, on behalf of ISO/IEC under copyright licence LN001327
More Information Request a demo
ISO/IEC 27001:2022 specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the Organisation.
It also includes the requirements of ISO/IEC 27002:2022 in the Annexes.
There are 234 controls in the framework. Applicability - Global.
More Information Request a demo
The ISO/IEC 27002 Information Security Standard is a comprehensive and internationally recognised framework designed for Organisation’s of all types and sizes to be used as a reference for determining and implementing the controls for information security risk treatment in an Information Security Management System (ISMS) based on ISO/IEC 27001.
It contains 1,249 controls. Applicability – Global.
More Information Request a demo
This Standard is the first technical standard that will be incorporated into the Government Functional Standard for Security in the UK. It defines the minimum security measures that Departments shall implement with regards to protecting their information, technology and digital services to meet the SPF and National Cyber Security Strategy obligations.
The content of the Standard is 'open' so that Departments can apply their own values. In our SAM framework we have adopted a 'best practice' to these values so that Department's are able to measure their compliance against a set of definitive requirements.
More Information Request a demo
This directive was created to improve the security of network and information systems across the UK with a focus on essential services.
The CAF consists of a collection of indicators of good practice structured around four main areas which form the framework's function areas.
The four CAFs are broken down into objectives which we have taken as our Categories and workplan content is derived from the NCSC NIS Guidance for each objective.
More Information Request a demo
The NIST CSF is a substantial standard designed to facilitate the protection of critical infrastructure in the US. NIST CSF 1.1 and NIST CSF 2.0 are available.
It is a set of cybersecurity activities, outcomes, and informative references that are common across critical infrastructure sectors that facilitate the alignment of cybersecurity activities with business requirements, risk tolerances and resources.
Our SAM framework is constructed to faithfully replicate the NIST CSF 1.1 structure with the controls being derived from NIST SP 800-53. The controls for NIST CSF are derived from the references provided within the NIST CSF 2.0 framework.
NIST CSF (Cybersecurity Framework) for Corporate Cybersecurity Compliance
The NIST CSF is a risk-based approach to managing cybersecurity risk and is composed of three parts: The Framework Core, the Framework Implementation Tiers and the Framework Profiles. Each Framework component reinforces the connection between business drivers and cybersecurity activities.
The SAM-NIST CSF Framework focuses on the Framework Core which is a set of cybersecurity activities, desired outcomes and applicable references that are common across critical infrastructure sectors. The core presents industry standards, guidelines and practices in a manner that allows for communication of cybersecurity activities and outcomes across the organisation from the executive level to the implementation/operations level. The NIST CSF 1.1 Framework Core consists of five concurrent and continuous Functions - Identify, Protect, Detect, Respond and Recover while the NIST CSF 2.0 framework adds Governance. When considered together these Functions provide a high-level, strategic view of the lifecycle of an organisation's management of cybersecurity risk. The Framework Core then identifies underlying key Categories and Subcategories for each function.
While the NIST CSF Framework is not exhaustive, it is extensible, allowing organisations, sectors and other entities to use sub-categories and controls that are cost-effective and efficient, and that enable them to manage their cybersecurity risk.
Using the SAM-NIST CSF Framework, organisations have the ability to demonstrate compliance to this standard and identify areas where remediation is required to improve the overall cybersecurity posture.
CYBERSECURITY INSURERS AND UNDERWRITERS
How do you measure and assess the cybersecurity fitness of your potential and current customers? Is this customer a risk worth insuring? You can use SAM to assess and measure how well a customer organisation manages cybersecurity.
More Information Request a demo
HIPAA (Health Insurance Portability and Accountability Act of 1996) determines the data privacy and security provisions for safeguarding medical information.
Our framework is structured around six function areas containing the 22 sections documented within the HIPAA Security Rule.
The controls have been strictly derived from NIST SP 800-66 HIPAA.
This framework is applicable to medical practices, hospitals and other primary care providers in the US.
More Information Request a demo
The NSW Cyber Security policy outlines the mandatory requirements to which all NSW government departments and Public Service agencies must adhere, to ensure cyber security risks to their information and systems are appropriately managed.
This is a small framework structured around the five mandated sections and includes 99 controls.
More Information Request a demo
The New Zealand Information Security Manual (NZISM) is the New Zealand Government's manual on information assurance and information systems security.
Assessing and tracking the implementation of NZISM with over 1690 requirements has, until now, been an onerous task so we created a SAM-NZISM framework in order to remove some of the pain and manage compliance.
This standard is applicable to Government Departments, their suppliers and service providers.
NEW ZEALAND GOVERNMENT CYBERSECURITY
MANAGE, TRACK AND REPORT IN REAL TIME, AND DEMONSTRATE COMPLIANCE WITH NZISM USING SAM for COMPLIANCE
The New Zealand Information Security Manual (NZISM) is the New Zealand Government's manual on information assurance and information systems security.
The NZISM is a practitioner’s manual designed to meet the needs of agency information security executives as well as vendors, contractors and consultants who provide services to agencies. It includes minimum technical security standards for good system hygiene, as well as providing other technical and security guidance for government departments and agencies to support good information governance and assurance practices.
The NZISM, while intended primarily for the use of government departments and agencies, and their service providers, will be equally useful for Crown Entities, Local Government bodies and private sector organisations.
SAM-NZISM includes approximately 1,690 controls relevent to the 'All Classifications' category and specifically excludes Secret and Top Secret.
More Information Request a demo
This standard was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally.
PCI-DSS provides a baseline of technical and operations requirements designed to protect account data and applies to all entities involved in payment card processing, including merchants, processors, acquirers, issuers and service providers.
PCI DSS also applies to all other entities that store, process or transmit cardholder data and/or sensitive authentication data.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. PCI DSS provides a baseline of technical and operational requirements designed to protect account data. PCI DSS applies to all entities involved in payment card processing - including merchants, processors, acquirers, issuers and service providers. PCI DSS also applies to all other entities that store, process or transmit cardholder data (CHD) and/or sensitive authentication data (SAD).
PCI DSS is broken down six overarching focus areas that contain twelve PCI DSS requirements.
The SAM-PCIDSS framework is designed around this structure and uses the defined controls as the basis for assessing compliance with the Standard.
If you would like to know whether you should comply with PCI DSS or would like more information, click on the buttons below to request further information or book a demonstration.
More Information Request a demo
This framework is designed for the Australian Prudential and Insurance industry and enables organisations to demonstrate compliance to the CPS 234 Standard as required by APRA.
This is a substantial standard that utilises the CPS 234 to define the nine function areas and the CPG 234 to define the Categories and Work Plan Objectives.
As this is an overarching standard we have derived the controls from a variety of sources including NIST SP 800-53, CIS Controls and ISO 27002.
MANAGE, TRACK AND REPORT IN REAL TIME, INFORMATION ASSET RISK AND DEMONSTRATE COMPLIANCE WITH CPS 234 USING SAM for COMPLIANCE
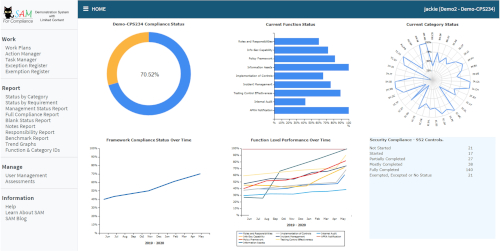 This Prudential Standard aims to ensure that an APRA-regulated entity takes measures to be resilient against information security incidents (including cyber-attacks) by maintaining an information security capability commensurate with information security vulnerabilities and threats and considered against your information assets.
This Prudential Standard aims to ensure that an APRA-regulated entity takes measures to be resilient against information security incidents (including cyber-attacks) by maintaining an information security capability commensurate with information security vulnerabilities and threats and considered against your information assets.
A key objective is to minimise the likelihood and impact of information security incidents on the confidentiality, integrity or availability of information assets, including information assets managed by related parties or third parties.
The key requirements of this Prudential Standard are that an APRA-regulated entity must:
- clearly define the information security-related roles and responsibilities of the Board, senior management, governing bodies and individuals;
- maintain an information security capability commensurate with the size and extent of threats to its information assets, and which enables the continued sound operation of the entity;
- implement controls to protect its information assets commensurate with the criticality and sensitivity of those information assets, and undertake systematic testing and assurance regarding the effectiveness of those controls; and
- notify APRA of material information security incidents.
The SAM CPS-234 Framework has been designed specifically for the Australian Financial and Insurance industry to enable organisations to demonstrate compliance to the Standard as required by APRA. With approximately 950 controls this is a substantial framework that utilises both the Standard and the Guide to create the structure. The controls have been derived from a variety of sources including NIST SP 800-53, CIS Controls and ISO 27002 with a foundation in APRA’s CPG 234 - Management of security risk in information and information technology (both 2010 and 2019).
More Information Request a demo
This framework is designed for New Zealand financial institutions and enables organisations to self-assess their cybersecurity posture in accordance with standards set by the Reserve Bank of New Zealand.
More Information Request a demo
The National Institute of Standards and Technology (NIST) Standard NIST SP 800-171 determines controls for the protection of controlled unclassified information in non federal information systems and organisations.
This is a very comprehensive standard requiring organisations to implement controls, systems and procedures and processes with an emphasis on the protection of information.
As NIST SP 800-171 is an overarching standard our framework utilises a variety of resources to define the controls including NIST SP 800-53, ISO-27002 and CIS Controls.
Any supplier of services to the US Government and any organisation serious about information protection should use this framework.
NIST SP 800-171 - Protecting Controlled Unclassified Information in nonfederal Information Systems and Organisations
This is an overarching Standard developed to protect Controlled Unclassified information (CUI) residing in nonfederal information systems and organisations. It is applicable to organisations providing services to Federal Government but also has wider applicability for larger corporates and businesses wanting a cybersecurity Standard with an Information Security perspective.
The responsibility of federal agencies to protect and ensure the control of CUI does not change when such information is shared with nonfederal partners. Therefore a similar level of protection is needed when CUI is processed, stored or transmitted by nonfederal organisations using nonfederal information systems.
The CUI security requirements have been developed based on three fundamental assumptions:
- Statutory and regulatory requirements for the portection of CUI are sonsistent, whether such information resides in federal information systems or nonfederal information systems, including the environments in which those systems operate;
- Safeguards implemented to protect CUI are sonsistent in both federal and non federal information systems and organisations; and
- The confidentiality impact value for CUI is no lower than moderate in accordance with the Federal Information Processing Standards (FIPS) Publication 199.
Additional assumptions impacting the development of the CUI security requirements also included:
- Organisations have information technology infrastructures in place, and are not necessarily developing or acquiring information systems specifically for the purpose of processing, storing or transmitting CUI;
- Organisations have specific safeguarding measures in place to protect their information which may also be sufficient to satisfy the CUI security requirements;
- Organisations can implement a variety of potential security solutions either directly or through the use of managed services to satisfy CUI security requirements; and
- Organisations may not have the necessary organisational structure or resorces to satisfy every CUI security requirement and may implement alternative, but equally effective, security measures to compensate for the inability to satisfy a particular requirement.
The Standard's security requirements are organised into fourteen families, each containing the requirements relating to the general security topic of the family. These are closely aligned with the minimum security requirements for federal information and information systems described in FIPS Publication 200.
The Standard provides a mapping to relevant security controls found within NIST SP 800-53 and ISO 27002, and we have derived our underlying controls for SAM-Protect from these sources as well as the CIS Controls, where applicable.
SAM-Protect is one of our larger frameworks and with its focus on information security, it is applicable to larger corporates and businesses that focus their security programmes on this aspect of cybersecurity.
If you would like to know whether SAM-Protect is applicable to your organisation or would like to view the content, click on the buttons below to request further information or book a demonstration.
More Information Request a demo
The ALGIM local government framework has been derived from SAM-Security content, but specifically customised for Local Government. This framework forms the foundation of the Local Government Cybersecurity Program which focuses on improving the overall cybersecurity posture of Local Government.
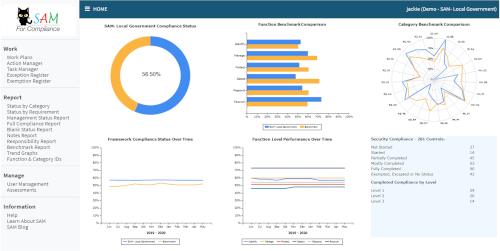 It features benchmarking of participants so that they can compare their performance against their peers, and annual awards recognising achievement in cybersecurity practice in accordance with pre-defined levels and improvement.
It features benchmarking of participants so that they can compare their performance against their peers, and annual awards recognising achievement in cybersecurity practice in accordance with pre-defined levels and improvement.
Local Government Cybersecurity Improvement Programme. Raising the bar on Local Government cybersecurity.
Cybersecurity has never been more important to local government than it is today. The cost of cybercrime is in the millions of dollars per quarter. Attacks by cybercriminals involving identity theft, exfiltration of information and extortion using ransomware and other techniques are occurring all around the world at unprecedented levels.
ALGIM's role involves creating opportunities and sharing knowledge to enable local government to thrive in an interconnected world and exploit the digital paradigm, however at the same time, organisational information and citizens’ personal information has become an internationally valuable commodity. One of ALGIM’s goals is to take a proactive approach and make a positive impact on the overall cybersecurity status of New Zealand Councils.
In conjunction with SAM for Compliance Ltd, ALGIM has defined a pragmatic cybersecurity framework specific to local government and based around the CIS Controls, that gives Councils the ability to manage and reduce organisational cybersecurity related risk. The objectives of the ALGIM Local Government Cybersecurity Improvement Programme are:
- Promoting excellence and cybersecurity best practice within Local Government
- Rewarding achievement and improvement in Local Government cybersecurity
- Identifying opportunities for training and awareness to improve cybersecurity knowledge within Local Government
- Benchmarking Local Government cybersecurity
Councils participating in the programme are able to identify whether they are above or below average as compared to their peers. ALGIM is able to identify areas where Councils are struggling to make headway and offer tailored workshops and training to assist if needed.
As part of the programme, Councils that demonstrate defined levels of achievement and improvement will receive awards at the ALGIM annual conference. The most improved small, medium and large Council is recognised each year and awarded at the ALGIM annual awards ceremony. Councils are also recognised for achievement based on a three tier structure - Levels 1 to 3.
To Register your interest, or sign up to the ALGIM Local Government Cybersecurity please click on the buttons below.
A SAM framework derived from SAM-Security specially for Non-Profit Organisations.
We've based the requirements on industry best practice, including our experience in helping develop and manage international cybersecurity standards.
SAM-Non-Profit allows you to assess, track, monitor and report in real-time, and enhances your ability to protect information assets from cyber-attack.
Donor data and program data are critical information assets - Protect your organisation from ransomware and malware!
Those who work in the service of others shouldn’t have to worry about losing donor data, or having services interrupted for clients and patients. As a not-for-profit you need to have full knowledge of where your cybersecurity protections are adequate or where there are gaps. When you need to show a new partner or donor how well you comply with cybersecurity standards you can do so quickly and easily with SAM’s real-time reporting.
Using SAM for Compliance to manage Cybersecurity Risk in Non-Profits
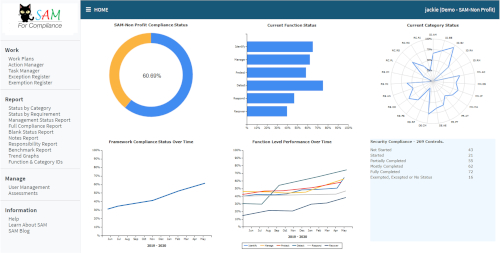 Where IT and cybersecurity are concerned what are some of your greatest challenges as a not-for-profit? - Resources, skills, time and money? Could the greatest challenge be getting a plan underway? Sometimes just starting can seem impossible. SAM-Nonprofit is a web based application accessible from your computer or mobile device. Our easy to understand, colourful Dashboard gives you an overview of how well your cybersecurity improvement programme is progressing. Within the system we'll even tell you how you have been trending over time.
Where IT and cybersecurity are concerned what are some of your greatest challenges as a not-for-profit? - Resources, skills, time and money? Could the greatest challenge be getting a plan underway? Sometimes just starting can seem impossible. SAM-Nonprofit is a web based application accessible from your computer or mobile device. Our easy to understand, colourful Dashboard gives you an overview of how well your cybersecurity improvement programme is progressing. Within the system we'll even tell you how you have been trending over time.
We've based the requirements on industry best practice, including our experience in helping develop and manage international cybersecurity standards. We've omitted items that nonprofits would be unable to achieve due to resource restraints to leave you with a set of simple, pragmatic action items that will protect your information and systems and help reduce risk.
Here is the good news; with SAM-Nonprofit, for about the price of lunch each day, you can assess, track, monitor and report in real-time, your ability to protect information assets from cyber-attack. We can have you up and running in no time and the system is easy and intuitive to use.
More Information Request a demo
Designed for the smaller non-profit organisations with less than 20 computers, this framework focuses on pragmatic requirements to achieve a basic level of cybersecurity.
It includes technology considerations for achieving appropriate cybersecurity measures but also includes common-sense procedures and processes that will further enhance your cybersecurity awareness and improve overall organisational security.
Smaller Nonprofits can take advantage of the same robust features in a Lite version
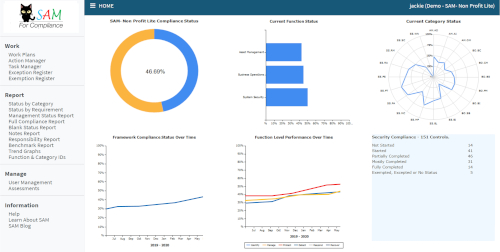 Nonprofits, like other businesses are not one-size-fits-all and neither is SAM. For smaller nonprofits that have less than 20 computers, we have SAM-Nonprofit Lite, a version that still provides the essential areas that will show you how well you protect your information assets, but has less requirements and a reduced footprint.
Nonprofits, like other businesses are not one-size-fits-all and neither is SAM. For smaller nonprofits that have less than 20 computers, we have SAM-Nonprofit Lite, a version that still provides the essential areas that will show you how well you protect your information assets, but has less requirements and a reduced footprint.
Take the first step in protecting your nonprofit from malware, ransomware and malicious individuals and click the button below to arrange a call with one of our representatives.
More Information Request a demo
Our general purpose cybersecurity framework. With approximately 280 requirements, this framework suits most medium sized organisations or those beginning their cybersecurity maturity journey.
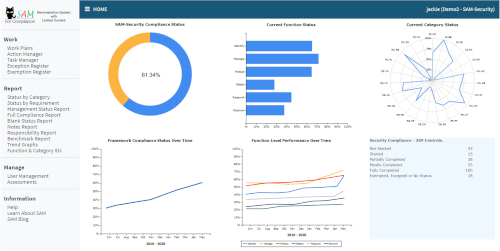 Well constructed, using an amended version of the NIST CSF functions and categories, with pragmatic, meaningful controls derived from CIS Controls, this framework is tailored for organisations that rely on a mixture of internal IT systems, internet, cloud, online services and email for administration and delivery of business operations.
Well constructed, using an amended version of the NIST CSF functions and categories, with pragmatic, meaningful controls derived from CIS Controls, this framework is tailored for organisations that rely on a mixture of internal IT systems, internet, cloud, online services and email for administration and delivery of business operations.
SAM-Security has been designed by us as a basic cybersecurity Standard suitable for implementation by small to medium enterprises.
The framework includes the CIS Controls and also covers additional areas such as Governance, Risk Assessment and Management, Response and Recovery.
With 269 controls, this framework is not difficult to implement and can easily be managed within existing resources. It is practical, pragmatic and effectively reports on the organisation's cybersecurity status in real-time. Features include Exemption and Exception Registers, Action and Task Managers and a variety of reports showing compliance at different levels.
This framework has a wide application and may be used by larger organisations that are just beginning their cybersecurity maturity journey.
If you would like to know whether SAM-Security would suit your organisation or would like to view the content, then request further information or book a demonstration.
More Information Request a demo
With over 25 years experience in managing small businesses, and the same amount of time working in the cybersecurity sector, we truly understand the challenges that face small business when it comes to protecting information, your business, and your reputation.
In today's world everyone is a target and small businesses are not immune from attack from cyber criminals, in fact they are more vulnerable, due to a lack of knowledge of cybersecurity issues and general lack of available resources.
This framework provides a basic set of approximately 140 simple-to-implement actions and checks that, if followed by staff and IT support, will reduce the level of cybersecurity risk in your business.
More Information Request a demo
The Department of Energy (DOE) developed the Cybersecurity Capability Maturity Model (C2M2) from the Electricity Subsector Cybersecurity Capability Maturity Model (ES-C2M2) Version 1.0 by removing sector-specific references and terminology. The ES-C2M2 was developed in support of a White House initiative led by the DOE, in partnership with the Department of Homeland Security (DHS), and in collaboration with private- and public-sector experts.
The C2M2 focuses on the implementation and management of cybersecurity practices associated with the information technology (IT) and operations technology (OT) assets and the environments in which they operate.
The framework implementation within SAM for Compliance has 10 Categories, 37 Work Plans and 312 controls. It includes all three maturity levels.
More Information Request a demo
This voluntary standard was developed using an industry-driven process and provides a foundational set of requirements designed to improve an organisation's cyber resilience and secure the assets critical to the operation of New Zealand’s control systems environments.
The requirements are principally derived from international best practice standards created by the North American Electric Reliability Corporate (NERC) and the National Institute of Standards and Technology (NIST).
The application of this standard will help prepare New Zealand’s critical infrastructure to address cyber security threats considering the nature, origin, scale, complexity, intensity and duration of these risks.
More Information Request a demo
The purpose of the Victorian Protective Data Security Standards (VPDSS) is to provide a set of criteria for the consistent application of risk-based practices to manage the security of Victorian government information. The Standards are issued under Parts 4 and 5 of the Privacy and Data Protection Act 2014.
This standard is applicable to Victorian public sector organisations.
More Information Request a demo